Metropolitan area network (MAN) is a network that expands into a metropolitan area such as a city or a region and exhibits high data rates, high reliability and low data loss. Wide area network is a network that expands beyond a metropolitan area. They interconnect with huge numbers of workstations and can cover large geographic distances, including the entire earth.
METROPOLITAN AREA NETWORK BASICS
- MANs has many of the same technologies and communications protocols found in LANs and WANs
- Support high-speed disaster recovery systems, real-time transaction backup systems, interconnections between corporate data centers and internet service providers, support high speed connections among government, business, medical, and educational facilities
- almost exclusively fiber-optic networks and capable of supporting data rates into the tens of millions and hundreds of millions bits per second
- cover greater distance than LANS
- can recover very quickly from a link or switch/router failure
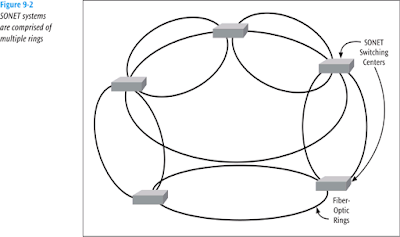
- MAN topologies are based on a ring
- the ability of a user to dynamically allocate more bandwidth on demand
1. SONET versus Ethernet
- Most MANs are SONET network built of multiple rings (for failover purposes)
- SONET is well-proven but complex, fairly expensive, and cannot be provisioned dynamically.
- Ethernet MANs generally have high failover times
- SONET is based upon T-1 rates and does not fit nicely into 1 Mbps, 10 Mbps, 100 Mbps, 1000 Mbps chunks, like Ethernet systems do.
- Metro Ethernet: is a data transfer service that can connect your business to another business using a standard Ethernet connection
- You may also connect your business with multiple businesses using a connection similar to a large local area network (Figure 9-4b)
- Thus, by simply sending out one packet, multiple companies may receive the data
- Neat thing about metro Ethernet is the way it seamlessly connects with a company’s internal Ethernet network(s)
WIDE AREA NETWORK BASICS
- WANs is a collection of computers and computer-related equipment interconnected to perform a given function typically using local and long-distance telecommunications systems
- Typically used to transfer bulk data between two endpoints and provide users with electronic mail services, access to database systems, and access to the internet
- WANs are very high speed with low error rates
- Usually follow a mesh topology
- A station is a device that interfaces a user to a network.
- A node is a device that allows one or more stations to access the physical network and is a transfer point for passing information through a network.
- A node is often a computer, a router, or a telephone switch.
- The sub-network or physical network is the underlying connection of nodes and telecommunication links.
Types of Network Structures
1. Circuit switched network:- A network cloud in which a dedicated circuit is established between the sender and receiver, and all data passes over this circuit
- The telephone system is a common example.
- The connection is dedicated until one party or another terminates the connection.
2. Packet switched network:
- All data messages are transmitted using fixed-sized packages, called packets
- More efficient use of a telecommunications lie since packets from multiple sources can share the medium
- Datagram packet-switched network, each data packet can follow its own possible unique course through the cloud
- Virtual Circuit packet-switched network create a logical path through the subnet and all packets from one connection follow this path
3. Broadcast network
- typically found in LANs, but occasionally found in WANs
- A workstation transmits its data and all other workstations "connected to the network hear the data. Only the workstations with the proper address will accept the data
Connection-oriented Versus Connectionless Network Application
- Connection oriented network application: provides some guarantee that information traveling through the network will not be lost and that the information packets will be delivered to the intended receiver, which is called Reliable Service
- A connection-oriented application requires both sender and receiver to create a connection before any data is transferred.
- Applications such as large file transfers and sensitive transactions such as banking and business are typically connection-oriented.
- A connectionless application does not create a connection first but simply sends the data.
- A connection oriented application can operate over both a circuit switched network or a packet switched network
- A connectionless application can also operate over both a circuit switched network or a packet switched network but a packet switched network may be more efficient
ROUTING
- Each node in a WAN is a router that accepts an input packet, examines the destination address, and forwards the packet on to a particular telecommunications line.
- A router must select the one transmission line that will best provide a path to the destination and in an optimal manner.
- Often many possible routes exist between sender and receiver.
- The communications network with its nodes and telecommunication links is essentially a weighted network graph.
- The edges, or telecommunication links, between nodes, have a cost associated with them.
- The cost could be a delay cost, a queue size cost, a limiting speed, or simply a dollar amount for using that link.
- The routing method, or algorithm, chosen to move packets through a network should be:
- Optimal, so the least cost can be found
- Fair, so all packets are treated equally
- Robust, in case link or node failures occur and the network has to reroute traffic.
- Not too robust so that the chosen paths do not oscillate too quickly between troubled spots.
1. Dijkstra's Least-cost Algorithm
- Is executed by each node and the results are stored at the node and sometimes shared with other nodes
- Calculation is time consuming so it is done on a periodic basis or when something is in the network changes
- By identifying all possible paths, it also identifies the lest cost path
2. Flooding Routing
- When a packet arrives at a node, the node sends a copy of the packet out every link except the link the packet arrived on.
- Traffic grows very quickly when every node floods the packet.
- To limit uncontrolled growth, each packet has a hop count. Every time a packet hops, its hop count is incremented. When a packet’s hop count equals a global hop limit, the packet is discarded
3. Centralized Routing
- One routing table is kept at a “central” node.
- Whenever a node needs a routing decision, the central node is consulted.
- To survive central node failure, the routing table should be kept at a backup location.
- The central node should be designed to support a high amount of traffic consisting of routing requests.
4. Distributed Routing
- Each node maintains its own routing table.
- No central site holds a global table.
- Somehow each node has to share information with other nodes so that the individual routing tables can be created.
- Possible problem with individual routing tables holding inaccurate information.
5. Adaptive Versus Fixed Routing
- With adaptive routing, routing tables can change to reflect changes in the network
- Static routing does not allow the routing tables to change.
- Static routing is simpler but does not adapt to network congestion or failures.
NETWORK CONGESTION
- When a network or a part of a network becomes so saturated with data packets that packet transfer is noticeably impeded, network congestion occurs.
- What can cause network congestion? Node and link failures; high amounts of traffic; improper network planning.
- When serious congestion occurs buffers overflow and packets are lost.
- An application can observe its own traffic and notice if packets are disappearing. If so, there may be congestion. This is called implicit congestion control
- The network can inform its applications that congestion has occurred and the applications can take action. This is called explicit congestion control
- Before making a connection, user requests how much bandwidth is needed, or if connection needs to be real-time
- Network checks to see if it can satisfy user request
- If user request can be satisfied, connection is established
- If a user does not need a high bandwidth or real-time, a simpler, cheaper connection is created
- This is often called connection admission control
3.
3.
3














No comments:
Post a Comment